Virtual Ciso
What Is a Virtual CISO?
A virtual Chief Information Security Officer is a senior-level executive who oversees an organization’s data, cyber, and technology security. The CISO’s responsibility is to develop, implement, and enforce security policies to protect critical data.
All businesses need a security leader who is responsible for overseeing technology, information, and data security-even if that person doesn’t have the title of CISO.
Small to mid-sized businesses (SMBs) find it more efficient to outsource the CISO role. This approach can help the company protect its intellectual property and data, along with its IT infrastructure.
- Cyber threats and attacks have grown rapidly since the pandemic and are continuing to rise at a rapid rate. Implementing the right security environment, strategy, and resources is critical for all businesses including SMBs.
- Businesses benefit from a CISO’s broad view of security. This technology leader understands how various aspects of security related to the IT systems, devices, and networks upon which the business operates and relies.
AA Networks has an elite internal security team to help implement the recommended improvements and increase operational efficiency. Helping your organization protect its sensitive information is our top priority.
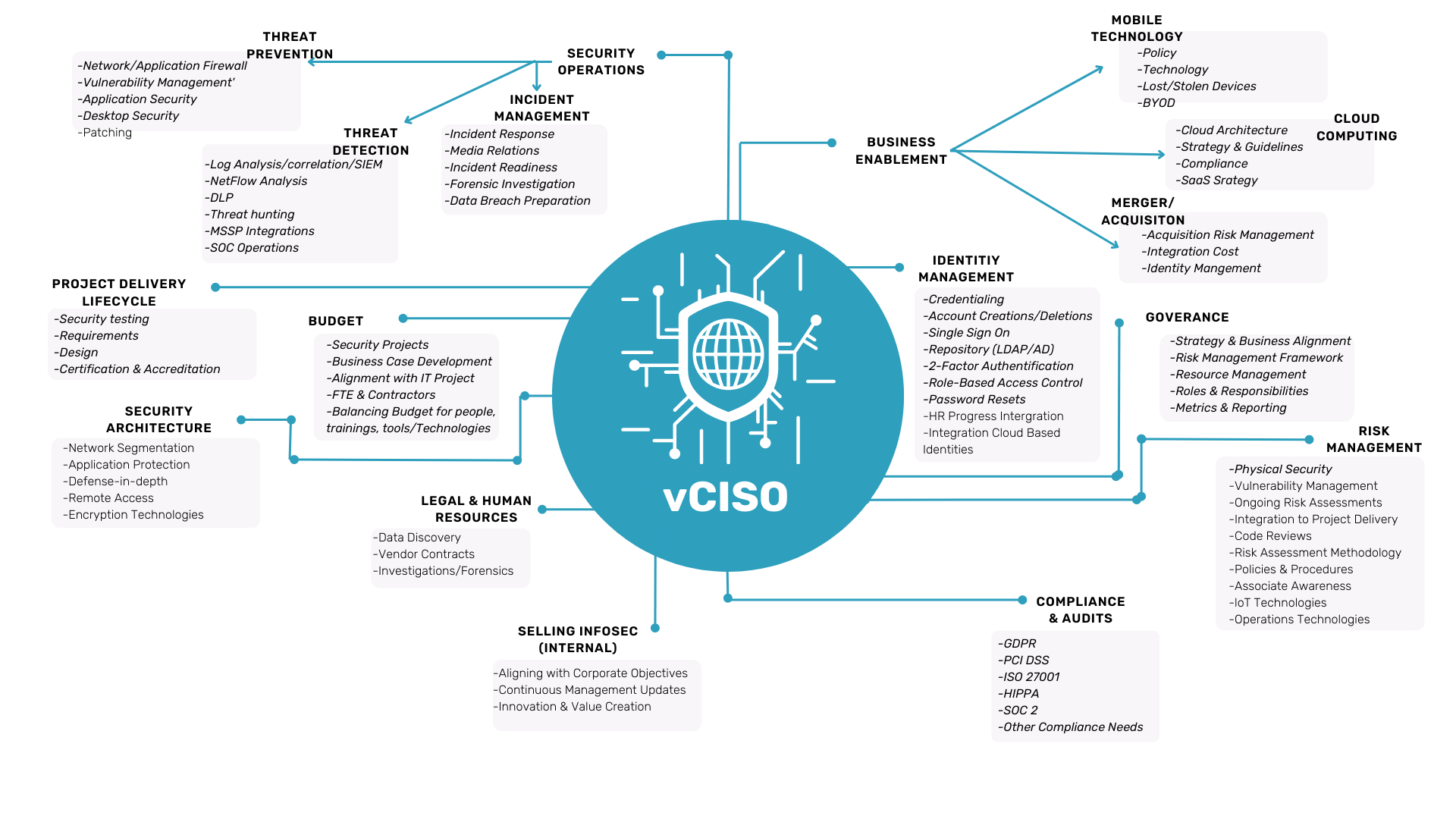
- We provide the vision, strategy, direction, and implementation of security for your organization. Helping you understand the strengths and weakness of your organization’s security by providing actionable recommendations, roadmaps, and mitigating the risk found in risk assessment findings.
- Our team provides high-security infrastructure-based policies and procedures based on industry standards, such as NIST SP 800-53, NIST SP 800-171, CMMC, HIPPA, PCI, ISO/IEC 27001.
- We provide a thorough assessment of your current infrastructure and business processes to identify any gaps in cybersecurity controls and provide a Plan of Action and Milestones (POAMs) to mitigate any identified risks associated with those gaps in a cost-effective and efficient manner.
STEPS
vCISO Security Program
1
Security Assessment
2
Security Operations Development
3
Security Talent Allocation/Training
4
Threat Modeling